Overview
Antigena SaaS neutralizes unpredictable attacks in cloud and collaboration tools.
From Microsoft Teams to SharePoint, Antigena SaaS responds with surgical precision when trusted cloud accounts are being used carelessly or for malicious purposes.
Unlike policy-based defenses, the technology takes action in light of a multidimensional understanding of digital behavior across hybrid and multi-cloud environments. This enables swift and targeted action that stops SaaS attacks while allowing normal business operations to continue unimpeded. Security operators investigating unusual SaaS activity can also trigger Darktrace Antigena actions directly as desired.
Neutralizes attacks others miss
AI stops insider threats, account takeover, and personnel risks
Decisions based on self-learning AI
Understands the human behind corporate cloud accounts
Responds in seconds
Reacts faster than human defenders and automated attacks
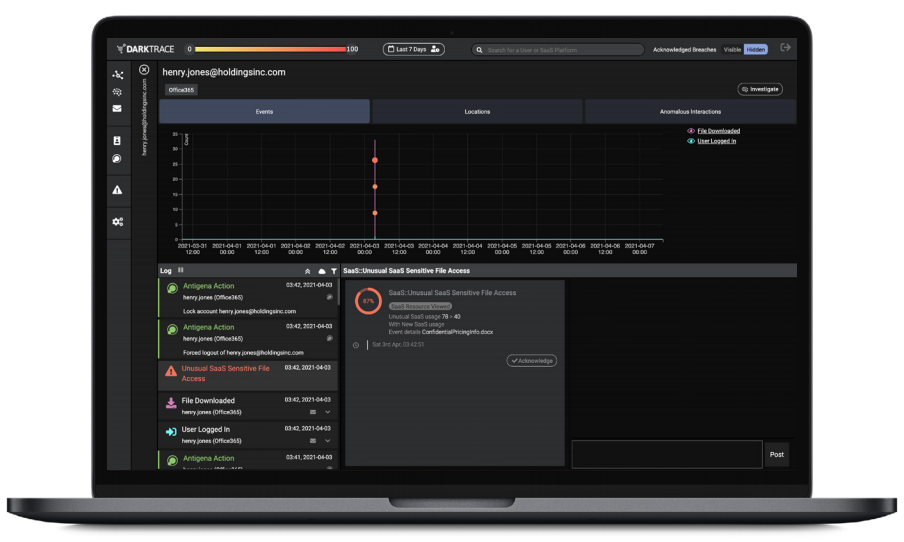
Darktrace SaaS Console
The Darktrace SaaS Console is a dedicated user interface designed to highlight malicious or risky behavior occurring across your diverse cloud footprint. This allows security teams to visualize and monitor security incidents and Antigena SaaS actions in one centralized location.
Features
AI protection for cloud & collaboration
Antigena SaaS protects your dynamic workforce from subtle attacks that evade static and siloed defenses.
Protecting the workforce with self-learning AI
From Microsoft Teams to SharePoint, Antigena SaaS responds with surgical precision when trusted cloud accounts are being used carelessly or for more malicious purposes.
Powered by self-learning AI, Autonomous Response takes dynamic action in seconds — not minutes — and well before SaaS attacks have time to escalate.
Stops subtle SaaS attacks
Antigena SaaS understands the multidimensional human behind corporate cloud accounts, adapting autonomously as the people and patterns in an organization evolve. Self-learning protection of this kind enables Antigena to adapt to the inherent flux of digital business, while neutralizing unpredictable attacks that evade static and siloed defenses — from accidental data leaks to savvy or disgruntled insiders.
Reacts surgically, in seconds
Unlike policy-based defenses, Antigena operates as an AI decision-making framework that takes action in light of a dynamic understanding of user behavior across hybrid and multi-cloud environments. This enables swift and targeted action that stops SaaS attacks while allowing the business to operate.
Darktrace SaaS Console
The Darktrace SaaS Console is a dedicated user interface designed to highlight malicious or risky behavior occurring across your diverse cloud footprint.
This allows security teams to visualize and monitor security incidents and Antigena SaaS actions in one centralized location.
Autonomous Response for Microsoft 365
Antigena SaaS operates as a fundamental technology in a wider Autonomous Response framework and self-learning platform. This means that organizations can seamlessly extend the scope of the technology to enable autonomous detection, investigation, and response across additional data sources and types of behavior at scale.
In many deployments, Antigena SaaS is deployed alongside Antigena Email to deliver extended protection of an organization’s Microsoft 365 environment. By analyzing inbound, outbound, and lateral email traffic, Antigena Email neutralizes targeted email campaigns and impersonation attacks that evade the email gateway.
Cyber AI
Malicious SaaS Administrator
Identifying malicious administrator activity in SaaS platforms is a critical security concern. Whether their motive is fraud, IP gain, or sabotage, administrators who take advantage of their position to damage the company may be one of the most insidious types of insider threats.
Managing SaaS user privileges and activity is already a challenge for security teams, with most defenses relying on simple rules and incompatible controls to monitor these complex environments. This static approach to security is often insufficient – a disquieting fact that is exacerbated when a trusted administrator becomes an insider threat.
Administrators typically have elevated privileges and understand SaaS platforms better than anyone, which means most native and third-party security tools will fail to see subtle malicious behavior. Because these tools have limited visibility, armed only with basic analytics and static policies, they are unable to spot the nuanced behavioral shifts that indicate a malicious administrator. Traditional SaaS security solutions are also siloed from the rest of the network, and therefore cannot connect workforce behaviors across an organization to illuminate the greater narrative of malicious activity when an insider becomes a threat.
This leaves companies vulnerable to serious data loss and damage to operations. Moreover, should customer or employee data be exposed, businesses likely face severe privacy and compliance violations, accompanied by reputational damage, legal liabilities, and financial burden. Considering the massive amount of sensitive data that passes through Salesforce accounts, or the business-critical information that may sit in Box environments, it is clear that organizations require a more adaptive and unified approach to threat detection in this area.
Cyber AI: Detecting Stealthy Insider Threats
Darktrace’s Cyber AI Platform ensures that malicious activity from administrators in SaaS environments is no longer a blind spot. Rather than using pre-configured rules, Darktrace Cyber AI analyzes all SaaS traffic with proprietary AI, building a deep understanding of normal workforce behavior for your entire organization. The power of self-learning Cyber AI allows Darktrace to identify even the most subtle deviations from normal that indicate an insider threat.
Instead of assuming trust, Darktrace Cyber AI uses its evolving knowledge of behavior in SaaS platforms to detect when insiders turn malicious, catching even those nefarious users with administrative privileges. Darktrace is also the industry’s only solution that can correlate activity across SaaS environments with the rest of the organization. This enables the technology to coordinate weak indicators of a threat across areas that have traditionally represented security siloes, providing even greater context and shining a light on workforce behaviors that show up in every corner of the digital business.
Case Study: Disgruntled IT Administrator
When an organization was forced to make a series of redundancies over the course of a single week, they neglected to take a fired IT administrator’s laptop, or to delete their corporate account. The former IT admin logged into one of their SaaS accounts and quickly downloaded many sensitive files – including contact details and credit card numbers from the customer database. They then attempted to secretly transfer the stolen files to a home server via one of the company’s regular data transfer services.
Because Darktrace dynamically analyzes logins and file access events across SaaS services, the system could immediately pick up on the unusually large file downloads and the exfiltration. Even though the disgruntled employee was still in the system as a legitimate administrator and used a familiar transfer service, Darktrace Cyber AI understood that the user’s behavior within the SaaS platform was highly unusual and an indication of a significant threat.
Subsequent investigation revealed that the malicious admin continually sought to exfiltrate the stolen SaaS files through several other methods, including with an internal server he had used regularly at the company. While the administrator’s use of this server may have seemed normal in a different context, Cyber AI was able to connect the dots between the disgruntled employee’s actions in the SaaS ecosystem and the corporate network, illuminating the full extent of this user’s malicious behavior.
While this activity from a supposedly trusted administrator easily evaded both traditional solutions and native SaaS security controls, Darktrace Cyber AI detected the threatening behavior within seconds. The system instantly alerted the security team and provided detailed and precise information about the nature of the compromise, prompting them to revoke his credentials and quickly retrieve and secure the data. With Darktrace’s complete, granular visibility and bespoke knowledge of normal behavior in SaaS platforms, the company was able to avoid any data loss, as well as serious compliance and digital trust consequences.
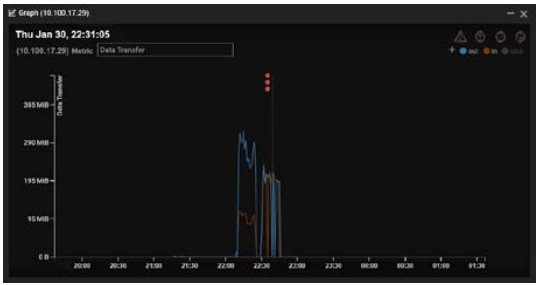
The Threat Visualizer showing a large spike in data transfers
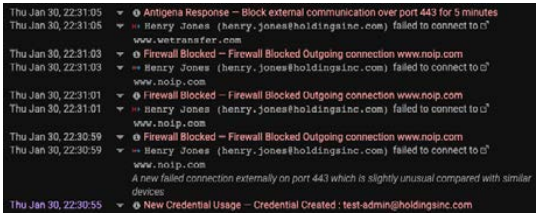
Darktrace Antigena actioning a targeted autonomous response
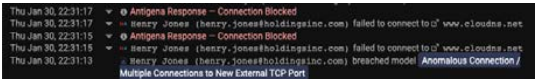
Antigena blocks the employee’s attempt to transfer files via the cloud
Compromised SaaS Credentials
Given the sheer amount of data that passes through SaaS environments and the speed of digital business afforded by these spaces, compromised credentials can allow threat actors to surreptitiously launch attacks that spread fast and far.
Today’s digital workforce leverages a wide variety of SaaS platforms to handle critical operations and sensitive information, from customer data and financial records to valuable intellectual property. A lack of visibility in SaaS accounts can expose the organization to operational disruption, data loss, and hefty compliance and remediation expenditures.
Criminals can gain access to corporate SaaS accounts in several ways, from social engineering and spear phishing attacks, to automated brute-force attempts, which can be extremely effective if employees have weak passwords or lack multi-factor authentication. Passwords can even be leaked inadvertently – for instance, if a user accidentally leaves login details in an open-source code repository. Yet whatever the method, threat actors are often just one successful attempt away from stealing the crown jewels of an organization.
Both native and third-party security tools lack the ability to spot subtle patterns of malicious behavior within SaaS platforms, instead relying on static rules and pre-defined policies. This approach leaves organizations with limited visibility and control over their SaaS infrastructure. Moreover, siloed security tools are unable to correlate workforce behaviors in SaaS with activity in the rest of the organization, and thus fail to see the full extent of an attack that involves compromised SaaS credentials.
Cyber AI: Identifying the Subtle Signs of Credential Compromise
It takes the immune system approach of Darktrace’s Cyber AI Platform to detect threat actors with compromised SaaS credentials. Just like the human body, Darktrace uses a bespoke understanding of ‘self’ for an organization and its workforce to identify subtle deviations from normal that indicate an emerging threat. Instead of relying on simple and static rules, Cyber AI builds a multi-dimensional understanding of normal workforce behavior in SaaS environments to detect the weak indicators of account compromise.
Even when an attacker hides behind legitimate SaaS credentials, Darktrace’s self-learning AI will still detect the subtle signs that the user behind the login is not who they appear to be, ensuring that the impact of attacks can be mitigated. By learning the normal ‘pattern of life’ of every user in the business, Darktrace is also the only solution that can correlate fragmented workforce behaviors in SaaS services with activity in the rest of the organization. With enterprise-wide context, organizations can avoid security siloes, using self-learning AI to see the larger incident and detect every step of an attack involving compromised SaaS credentials.

Case Study: Microsoft 365 Compromise and SharePoint Infiltration
At a US-based insurance company, Darktrace Cyber AI’s bespoke knowledge of workforce behavior and visibility across SaaS platforms was crucial for stopping an attack that started with a compromised Microsoft 365 account.
When a threat actor successfully logged in to one of the client’s Microsoft 365 accounts from an IP address located in the United Arab Emirates, Cyber AI identified the behavior as anomalous, as no other Microsoft 365 accounts had ever been observed logging in from this IP address. Four days later, another rare IP located in the UAE was seen accessing the same compromised account. This time, the threat actor set up a new email rule, and further used their illegitimate access to read and write to files on the user’s personal SharePoint account.
Darktrace Cyber AI had not previously seen any other user accounts communicating with UAE-based IPs from the particular network identified in these incidents, indicating that the observed behavior was highly unusual for the customer and the result of compromise.
While the customer’s legacy tools only allowed them to see the threat when changes were made to the compromised account that broke the pre-configured rules, Darktrace Cyber AI picked up on the anomalous behavior as soon as it occurred and clearly illuminated the attacker’s movement between SaaS services. Darktrace was able to alert the security team immediately of the earliest stages of the attack, shining a light on every detail and assuring the threat was neutralized before serious damage could occur.
Darktrace Cyber AI is designed to protect the dynamic employees in your organization – no matter where they work, or the nature of their applications.